Security
category and roles
This page describes the wiki security. We used fine-grained access control by using Access control category markings on our pages.
We have the following Access control categories from category:Access Control:
- category:trainer
- category:student
- category:projects
- category:lesson
- category:public
- category:private
- category:user:t - note any user may be used
When a page has a category:Access Control then a user may access if they are in certain groups:
| category | group |
|---|---|
| category:trainer | trainer sysop |
| category:student | student sysop |
| category:projects | projects sysop |
| category:lesson | lesson sysop |
| category:public | all users |
| category:private | private sysop |
| e.g. category:user:t | user:t sysop |
🚩 Note the sysop reflects as administrator in the wiki Special:SpecialPages UI.
🚩 Note a page may be made public by placing the special category:public on the page.
🚩 Note we have organised the wiki pages into category:student for student access, and category:trainer for trainer and support user access.
Users are provided with rights when their account is made, and the administrator will be able to select the category:Access Control groups as shown in the screen-shot below.
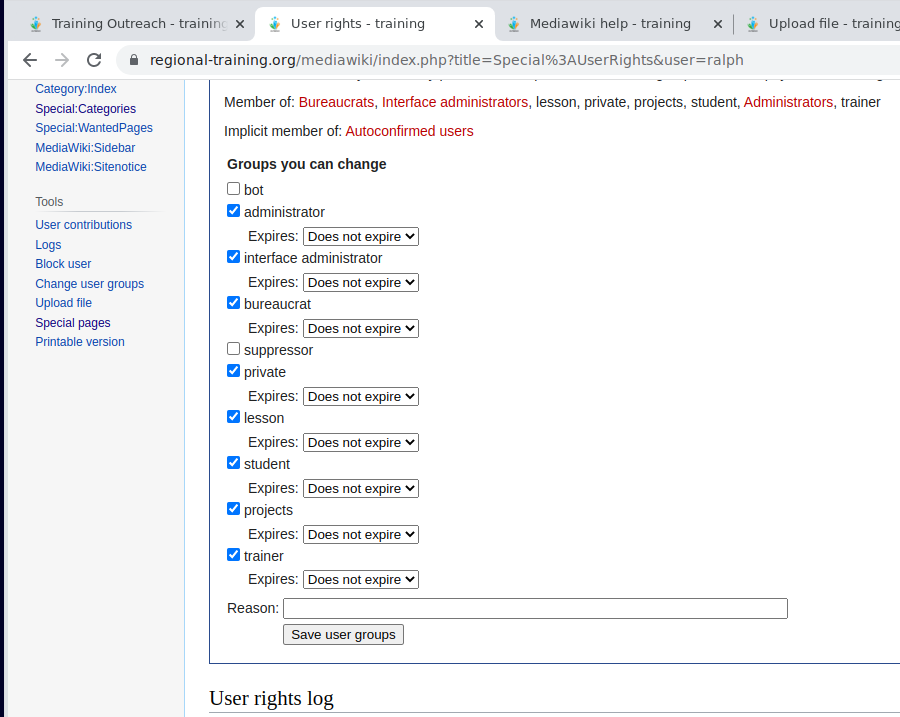
🚩 Note there are special exclusive category:user:... categories that allow a user to protect their own page from access by other users exclusively.
☢ Do not provide a regular user with the group private, it is best that trainers also do not have the private group either, use category:trainer to provide them with access to pages. The private marking is used to prevent a page from being published because it contains something that needs redaction ,or has identifying information you only want a sysop to be able to access.
network communication
A reverse proxy nginx server has been established to serve content using SSL/TLS with verifiable certificates. The reverse proxy server forwards data (on an internal network) to an apache2 http mediawiki server over a TLS tunnel, so at no time is any network communication in the clear, data is always covered by encryption. We have various intrusion detection in or edge router and supporting servers too.
logging
Notice that the Special:Log contains a log of all audit activities performed in the wiki.
The apache2 webserver also logs access via
- /data/training-wiki/www/log/acess.log and
- /data/training-wiki/www/log/error.log
I will be extending the mediawiki to audit when an anonymous user is asked to login so we can do intrusion detection. This normally only results in a status code 200 in the web-server response when the Login prompt message is returned, permitting the user a log in attempt.
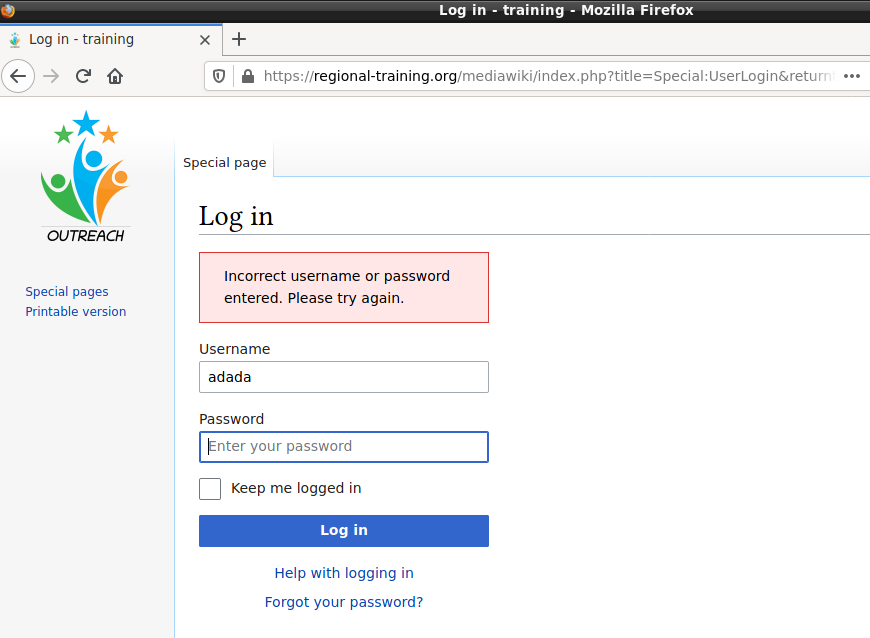
A failed login attempt results in a return to Special:BadTitle
Access control
pages
Wiki page fine-grained Access control is implemented by marking pages with special categories and assigning users to an associated group.
- edit LocalSettings.php and set the no public access for edit, read, createpage:
# SECURITY prevent public privileges $wgReadPermission['*']['read'] = false; $wgGroupPermissions['*']['edit'] = false; $wgGroupPermisisons['*']['createpage'] = false;
- install the Access Control code as an extension e.g. int file extensions/rabcg/RestrictAccessByCategoryAndGroup.php
access rules
The extension enforces the following rules:
- category:public pages are accessible to all, unless they are marked with:
- pages may have restricted edit when [marked]] with:
- category:edit:user: user-name.
- category:edit: group-name.
- white-listed pages are always accessible they are not marked private or restricted by a category:edit: marking.
- These Special: pages are also accessible to anonymous users:
- Special:Login
- Special:Logout
- Special:UserLogin
- Special:UserLogout
- Special:Badtitle
- Special:Random
- Special:RecentChanges
- Special:Version
- Special:AllPages
- Special:Search - added 2023-06-08 so unauthenticated users can search the category:Public indexed pages for content.
- are always accessible
- any administrator (sysop) can access any page - to permit oversight, abuse investigation and redaction operations.
- any page marked with category:public is accessible by anonymous, or other authenticated users when there is no exclusion category:user: marking.
- any pages without a category are not publicly accessible unless they are white listed; they are accessible only via authenticated logged-in users.
- category:private is an exclusive access control - no other private category will provide access to the page, and a user must have the private role or be a sysop to access the page.
- category:User: is an exclusive Access control to make pages accessible by that user or a sysop only.
See the Access Control code.
🚩 Note: You can use test pages to test Access control marking and roles.
🚩 Note: when you mark pages containing images and media with category:public those files are available to the public as well. However, a hyperlink is included to the File:<name> in the opage content and unless those File: pages are marked with category:public too they will not be available to anonymous users. This will break the web-bot and crawlers and lower your SEO unless you also mark the File: as public. When this is done the media file will be displayed in the category:public index.
media
Media/image access can be secured by making changes to apache2 to prevent direct access to the images director and to the mediawiki configuration to prevent public access, by forcing image access via img_auth.php:
- edit LocalSettings.php and set the no public access for
# SECURITY prevent public privleges $wgReadPermission['*']['read'] = false; $wgGroupPermissions['*']['edit'] = false; $wgGroupPermisisons['*']['createpage'] = false;
- edit LocalSettings.php and make image loading go through img_auth.php
$wgUploadPath = "$wgScriptPath/img_auth.php";
- edit apache2/etc/sites-available/region-training.org.conf and include a Deny from all section for the images directory
<Directory /data/training-wiki/www/mediawiki/images>
Deny from all
</Directory>
See Also
- https://www.mediawiki.org/wiki/Security_issues_with_authorization_extensions
- https://www.mediawiki.org/wiki/Manual:Security
- https://www.mediawiki.org/wiki/Manual:Preventing_access
- https://www.mediawiki.org/wiki/Manual:Configuring_file_uploads
- https://www.mediawiki.org/wiki/Extension:AccessControl
- https://www.mediawiki.org/wiki/Category:User_rights_extensions
- https://www.mediawiki.org/wiki/Extension:ImageFilter
- image_auth
categories
☢ Do not mark this page as category:private. Currently this page is marked category:Public which may change in the future.
